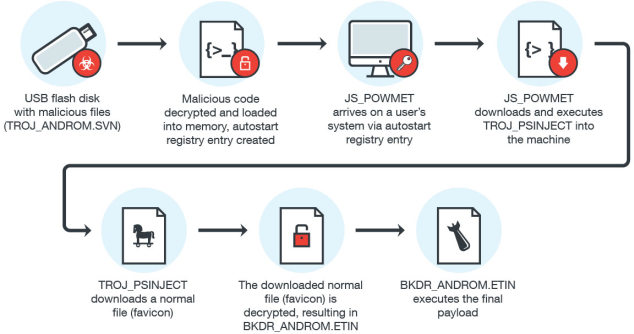
Trend Micro warns for a backdoor that doesn't write any files to the hard disk, which means it's relatively hard to detect and analyse. For a while it was unknown how the malware was distributed. It was previously thought the malware was downloaded by the user or installed with other malware. But Trend Micro now discovered the distribution goes through USB sticks.
The USB sticks contain shortcuts with the same name as the USB stick. As soon as the user opens a shortcut, malcious code is executed in the system's memory and an autostart value is added to the Windows registry that downloads the Powmet Trojan. In its turn, the Trojan downloads a Powershell script that downloads the backdoor on the system.
During the entire infection routine no files are written to the HDD. According to Trend Micro this method is pretty unique.
The company doesn't provide any information on where the USB sticks were found and how they got there. The backdoor is mainly found on systems in Asia and the Pacific.