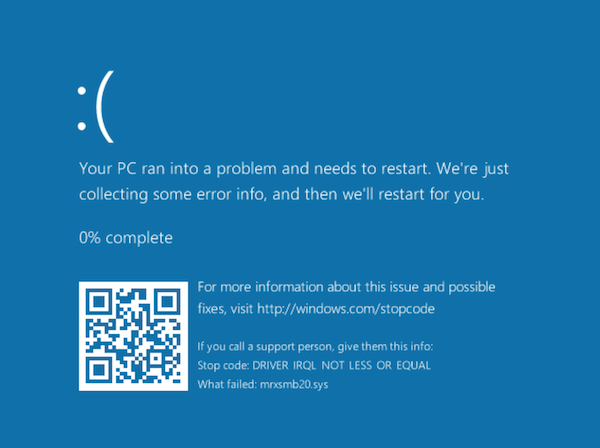
A vulnerability in Windows 10 allows attackers to crash computers running the operating system, according to security researchers from the CERT Coordination Center (CERT/CC) of the Carnegie Mellon University. Microsoft has not patched the issue. Also Windows 8.1 is vulnerable.
The vulnerability exploits the SMB networking protocol that allows Windows computers to connect to network drives, printers and other data. A memory corruption bug in the SMB implementation makes it possible to complete crash Windows 8.1 and Windows 10 systems when they connect to a malcious SMB server. When the bug is exploited the computer will show a Blue Screen of Death (BSOD).
According to the researchers it's unclear whether the bug can only be exploited to crash computers or that it will also be possible to take control over the system. In theory it could be possible for attackers to execute arbitrary code with Windows kernel privileges.
CERT/CC adds that there are numerous of methods that can be used to trigger a Windows computer to connect to an SMB server.
The Internet Storm Center warns that there is an exploit for the vulnerability available 'in the wild' which can be used to crash Windows 10 computers. The exploit was designed to crash Windows 2012 and 2016 computers but has been confirmed to also have effect on Windows 10 devices.
Currently there is no patch for the issue, users who want to protect themselves from this vulnerability can temporarily block outgoing SMB connections through TCP ports 139 and 445 and UDP ports 137 and 138 of the local network to a WAN.